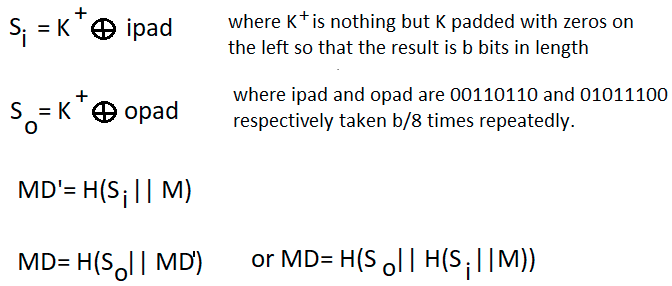FAQs
Hash-based message authentication code (or HMAC) is a cryptographic authentication technique that uses a hash function and a secret key. With HMAC, you can achieve authentication and verify that data is correct and authentic with shared secrets, as opposed to approaches that use signatures and asymmetric cryptography.
What type of algorithm is HMAC? ›
HMAC algorithm stands for Hashed or Hash-based Message Authentication Code. It is a result of work done on developing a MAC derived from cryptographic hash functions. HMAC is a great resistance towards cryptanalysis attacks as it uses the Hashing concept twice.
How many keys does HMAC use? ›
HMAC keys can only be used to make requests to the XML API, not the JSON API. You can have a maximum of 5 HMAC keys per service account.
What is HMAC and explain its advantages over MAC? ›
What makes HMAC more secure than MAC is that the key and the message are hashed in separate steps. It can also be proven secure based on the cryptographic strength of the underlying hash function, the size of its hash output length and on the size and strength of the secret key used.
Where is HMAC used? ›
HTTPS, SFTP, FTPS, and other transfer protocols use HMAC. The cryptographic hash function may be MD-5, SHA-1, or SHA-256. Digital signatures are nearly similar to HMACs i.e they both employ a hash function and a shared key.
How does HMAC algorithm work? ›
Hash-based Message Authentication Code (HMAC) is a message authentication code that uses a cryptographic key in conjunction with a hash function. Hash-based message authentication code (HMAC) provides the server and the client each with a private key that is known only to that specific server and that specific client.
What is HMAC header? ›
HMAC (hash-based message authentication code) is used to verify that a request is coming from an expected source and that the request has not been tampered with in transit.
Is an HMAC a signature? ›
HMAC Signing is an access token method that adds another level of security by forcing the requesting client to also send along a signature that identifies the request temporally to ensure that the request is from the requesting user, using a secret key that is never broadcast over the wire.
What is used when creating a HMAC? ›
Any cryptographic hash function, such as SHA-2 or SHA-3, may be used in the calculation of an HMAC; the resulting MAC algorithm is termed HMAC-X, where X is the hash function used (e.g. HMAC-SHA256 or HMAC-SHA3-512).
How long is a HMAC key? ›
The minimum length for an MD5 HMAC key is 16 bytes. A key longer than 16 bytes does not significantly increase the function strength unless the randomness of the key is considered weak. A key longer than 64 bytes will be hashed before it is used. An SHA-1 key is used for HMAC operations.
HMAC is a MAC/keyed hash, not a cipher. It's not designed to be decrypted. If you want to encrypt something, use a cipher, like AES, preferably in an authenticated mode like AES-GCM. Even knowing the key, the only way to "decrypt" is guessing the whole input and then comparing the output.
How is HMAC verified? ›
After receiving the message, your app should verify the HMAC signature by attempting to re-create one or both of the signatures by hashing the raw message body with one or both of the app's HMAC keys. To verify the signatures: Extract the text of the UTF-8 payload as an array of bytes.
Which statement is a feature of HMAC? ›
Which statement is a feature of HMAC? HMAC uses protocols such as SSL or TLS to provide session layer confidentiality.
How do I generate HMAC keys? ›
Create an HMAC key
Click Settings. Select the Interoperability tab. Click + Create a key for a service account. Select the service account you want the HMAC key to be associated with.
Does HMAC use private key? ›
Hash-based message authentication code (or HMAC) is a cryptographic technique that combines public keys, private keys, and a hash into a mix hackers can't unpack.
When was HMAC created? ›
HMAC is a MAC algorithm designed by Bellare et al. [1] in 1996. A MAC algorithm is a cryptographic algorithm that computes a complex function of a data string and a secret key; the resulting MAC value is typically appended to the string to protect its authenticity.
How is HMAC different from MAC? ›
The main difference between MAC and HMAC is that MAC is a tag or a piece of information that helps to authenticate a message, while HMAC is a special type of MAC with a cryptographic hash function and a secret cryptographic key. Cryptography is the process of sending data securely from the source to the destination.
What is HMAC error? ›
"HMAC Authentication Error" HMAC authentication errors occur when there is an issue with the HMAC token. Perform the following troubleshooting steps: Attempt to enroll with a different device to see if you receive the same error. Reinstall the Agent and then try enrolling the device again.
What is HMAC and RSA? ›
It is my understanding that HMAC is a symmetric signing algorithm (single secret key) whereas RSA is an asymmetric signing algorithm (private/public key pair).
How does HMAC work in Java? ›
HMAC is a cryptographic method that guarantees the integrity of the message between two parties. HMAC algorithm consists of a secret key and a hash function. The secret key is a unique piece of information or a string of characters. It is known both by the sender and the receiver of the message.
HMAC (hash-based message authentication code) is used to verify that a request is coming from an expected source and that the request has not been tampered with in transit.
What is HMAC and SHA? ›
HMACSHA256 is a type of keyed hash algorithm that is constructed from the SHA-256 hash function and used as a Hash-based Message Authentication Code (HMAC).
What is the output of HMAC ()? ›
The size of the output of HMAC is the same as that of the underlying hash function (e.g., 256 and 512 bits in the case of SHA-256 and SHA3-512, respectively), although it can be truncated if desired. HMAC does not encrypt the message. Instead, the message (encrypted or not) must be sent alongside the HMAC hash.
How do I create a HMAC key? ›
Click Settings. Select the Interoperability tab. Click + Create a key for a service account. Select the service account you want the HMAC key to be associated with.
What are the disadvantages of HMAC? ›
6) Disadvantages
- As HMAC makes use of the shared key, If there is a compromise in the key of sender or receiver, it makes the job of creating unauthorised messages easier for attackers.
- There is also a need for periodic refreshments of keys, which adds to its disadvantage.
HMAC(Hash-based message authentication code) is a message authentication code that uses a cryptographic hash function such as SHA-256, SHA-512 and a secret key known as a cryptographic key. HMAC is more secure than any other authentication codes as it contains Hashing as well as MAC.
What is the difference between HMAC and MAC? ›
The main difference between MAC and HMAC is that MAC is a tag or a piece of information that helps to authenticate a message, while HMAC is a special type of MAC with a cryptographic hash function and a secret cryptographic key. Cryptography is the process of sending data securely from the source to the destination.