Table of contents
About security audits
A security audit is an assessment of package dependencies for security vulnerabilities. Security audits help you protect your package's users by enabling you to find and fix known vulnerabilities in dependencies that could cause data loss, service outages, unauthorized access to sensitive information, or other issues.
Running a security audit with npm audit
Note: The npm audit command is available in npm@6. To upgrade, run npm install npm@latest -g.
The npm audit command submits a description of the dependencies configured in your package to your default registry and asks for a report of known vulnerabilities. npm audit checks direct dependencies, devDependencies, bundledDependencies, and optionalDependencies, but does not check peerDependencies.
npm audit automatically runs when you install a package with npm install. You can also run npm audit manually on your locally installed packages to conduct a security audit of the package and produce a report of dependency vulnerabilities and, if available, suggested patches.
- On the command line, navigate to your package directory by typing
cd path/to/your-package-nameand pressing Enter. - Ensure your package contains
package.jsonandpackage-lock.jsonfiles. - Type
npm auditand press Enter. - Review the audit report and run recommended commands or investigate further if needed.
Resolving EAUDITNOPJSON and EAUDITNOLOCK errors
npm audit requires packages to have package.json and package-lock.json files.
- If you get an
EAUDITNOPJSONerror, create apackage.jsonfile by following the steps in "Creating a package.json file". - If you get an
EAUDITNOLOCKerror, make sure your package has apackage.jsonfile, then create the package lock file by runningnpm i --package-lock-only.
Reviewing and acting on the security audit report
Running npm audit will produce a report of security vulnerabilities with the affected package name, vulnerability severity and description, path, and other information, and, if available, commands to apply patches to resolve vulnerabilities. For more information on the fields in the audit report, see "About audit reports"
Security vulnerabilities found with suggested updates
If security vulnerabilities are found and updates are available, you can either:
- Run the
npm audit fixsubcommand to automatically install compatible updates to vulnerable dependencies. - Run the recommended commands individually to install updates to vulnerable dependencies. (Some updates may be semver-breaking changes; for more information, see "SEMVER warnings".)
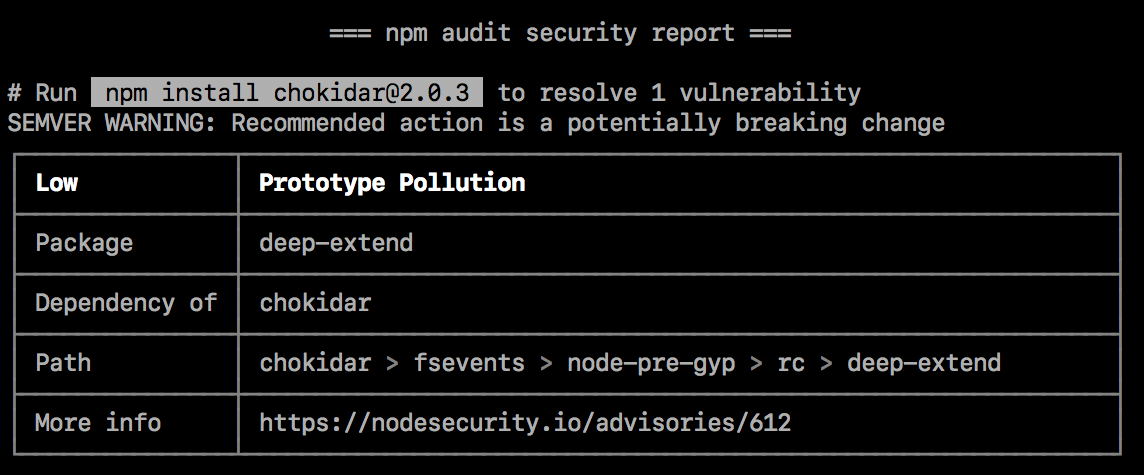
SEMVER warnings
If the recommended action is a potential breaking change (semantic version major change), it will be followed by a SEMVER WARNING that says "SEMVER WARNING: Recommended action is a potentially breaking change". If the package with the vulnerability has changed its API, you may need to make additional changes to your package's code.
Security vulnerabilities found requiring manual review
If security vulnerabilities are found, but no patches are available, the audit report will provide information about the vulnerability so you can investigate further.
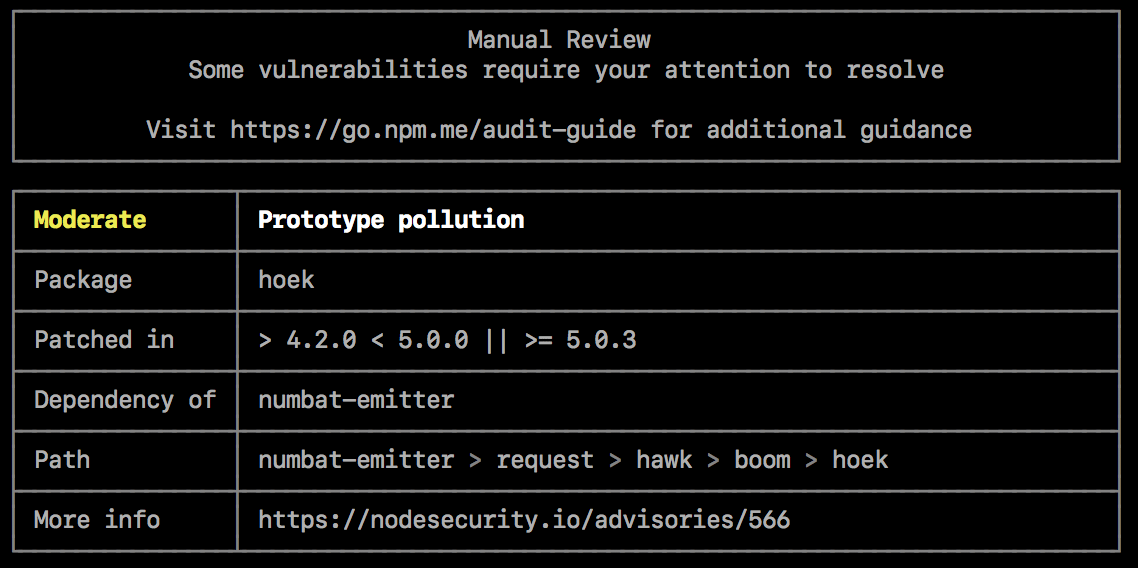
To address the vulnerability, you can
- Check for mitigating factors
- Update dependent packages if a fix exists
- Fix the vulnerability
- Open an issue in the package or dependent package issue tracker
Check for mitigating factors
Review the security advisory in the "More info" field for mitigating factors that may allow you to continue using the package with the vulnerability in limited cases. For example, the vulnerability may only exist when the code is used on specific operating systems, or when a specific function is called.
Update dependent packages if a fix exists
If a fix exists but packages that depend on the package with the vulnerability have not been updated to include the fixed version, you may want to open a pull or merge request on the dependent package repository to use the fixed version.
- To find the package that must be updated, check the "Path" field for the location of the package with the vulnerability, then check for the package that depends on it. For example, if the path to the vulnerability is
@package-name > dependent-package > package-with-vulnerability, you will need to updatedependent-package. - On the npm public registry, find the dependent package and navigate to its repository. For more information on finding packages, see "Searching for and choosing packages to download".
- In the dependent package repository, open a pull or merge request to update the version of the vulnerable package to a version with a fix.
- Once the pull or merge request is merged and the package has been updated in the npm public registry, update your copy of the package with
npm update.
Fix the vulnerability
If a fix does not exist, you may want to suggest changes that address the vulnerability to the package maintainer in a pull or merge request on the package repository.
- Check the "Path" field for the location of the vulnerability.
- On the npm public registry, find the package with the vulnerability. For more information on finding packages, see "Searching for and choosing packages to download".
- In the package repository, open a pull or merge request to make the fix on the package repository.
- Once the fix is merged and the package has been updated in the npm public registry, update your copy of the package that depends on the package with the fix.
Open an issue in the package or dependent package issue tracker
If you do not want to fix the vulnerability or update the dependent package yourself, open an issue in the package or dependent package issue tracker.
- On the npm public registry, find the package with the vulnerability or the dependent package that needs an update. For more information on finding packages, see "Searching for and choosing packages to download".
- In the package or dependent package issue tracker, open an issue and include information from the audit report, including the vulnerability report from the "More info" field.
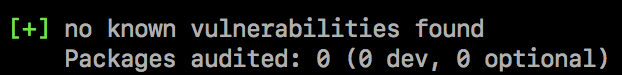
No security vulnerabilities found
If no security vulnerabilities are found, this means that packages with known vulnerabilities were not found in your package dependency tree. Since the advisory database can be updated at any time, we recommend regularly running npm audit manually, or adding npm audit to your continuous integration process.
Turning off npm audit on package installation
Installing a single package
To turn off npm audit when installing a single package, use the --no-audit flag:
npm install example-package-name --no-auditFor more information, see the npm-install command.
Installing all packages
To turn off npm audit when installing all packages, set the audit setting to false in your user and global npmrc config files:
npm set audit falseFor more information, see the npm-config management command and the npm-config audit setting.

